login
Can be used in
proxy, serviceProxy, transport, beans
Syntax
<login path="string" location="string" > user data provider [session manager] [account blocker] token provider </rest2Soap>
Overview
The login interceptor can be used to restrict and secure end user access to an arbitrary web application.
Users firstly have to authenticate themselves against a directory server using a username and password. Secondly, a numeric token is then sent to the user’s cell phone using a text message service. After token verification, access to the web application is granted for the user’s session. Single Sign On can easily be realized using a small source code extension or modification of a web application.
Sample Configuration
<login path="/login/" location="file:c:/work/login/">
<ldapUserDataProvider
url="ldap://192.168.2.100"
base="dc=predic8,dc=de"
searchPattern="(cn=%LOGIN%)">
<map>
<attribute from="telephoneNumber" to="sms" />
<attribute from="uidNumber" to="header-X-Security-UID" />
</map>
</ldapUserDataProvider>
<telekomSMSTokenProvider
user="predic8"
password="secret" />
</login>
<login path="/login/" location="file:c:/work/login/">
<ldapUserDataProvider
url="ldap://192.168.2.100"
base="dc=predic8,dc=de"
binddn="cn=Manager,dc=predic8,dc=de"
bindpw="secret"
searchPattern="(cn=%LOGIN%)"
searchScope="subtree"
timeout="1000"
connectTimeout="1000"
readAttributesAsSelf="true" >
<map>
<attribute from="telephoneNumber" to="sms" />
<attribute from="uidNumber" to="header-X-Security-UID" />
</map>
</ldapUserDataProvider>
<sessionManager
cookieName="SESSIONID"
timeout="300000" />
<accountBlocker
afterFailedLogins="5"
afterFailedLoginsWithin="9223372036854775807"
blockFor="3600000"
blockWholeSystemAfter="1000000" />
<telekomSMSTokenProvider
user="predic8"
password="secret"
prefixText="Token: "
normalizeTelephoneNumber="true" />
</login>
Explanation
The login interceptor combines 4 modules to implement its functionality. One implementation of each of the 4 module types is required. (The session manager and account blocker have default implementations.)
The user data provider checks user passwords and provides additional data for each user (e.g. cell phone number, Single Sign On data, etc.).
The session manager tracks the users' sessions across different HTTP requests (e.g. using a session cookie).
The account blocker tracks the number of failed login attempts and might block future login attempts for a specified amount of time.
The token provider generates the numeric token (possibly transmitting it to the user via a secondary channel like text messaging).
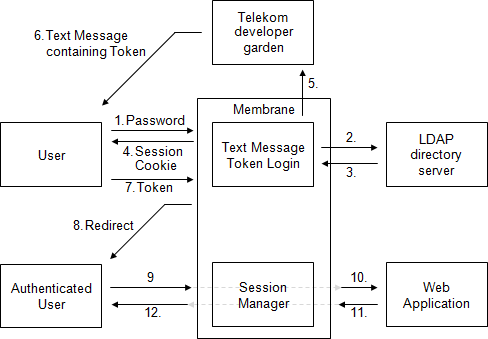
(Whether text messages and LDAP is actually used depends on the configuration. Alternatives are possible.)
The login interceptor realizes the login workflow. If all information entered by the user is valid, the workflow is as follows:
- The unauthenticated user is redirected to a login dialog.
- The user enters her username and password. (Step 1.)
- (A numeric token is sent to the user via text message, in case the telekomSMSTokenProvider is used. Steps 5 and 6.)
- The user enters her token. (Step 7.)
- The user is redirected to the originally requested URL (or a generic URL, in case the login dialog was directly requested). (Step 8.)
Configuration of the Login Dialog
The login dialog uses the context path specified by the path attribute of the login interceptor.
The location attribute points to a location (for example, a directory) where a template of the login dialog is located in a file called index.html. This file should at least contain a snippet similar to the following code:
${if error}
<p> Fehler: <span style="color:red;">
${if error='INVALID_PASSWORD'}
Ungültiges Passwort.
${else}
${if error='INTERNAL_SERVER_ERROR'}
Interner Fehler.
${else}
${if error='INVALID_TOKEN'}
Ungültiges Token.
${else}
${if error='ACCOUNT_BLOCKED'}
Ihr Zugang ist temporär gesperrt.
${else}
${error}
${end}
${end}
${end}
${end}
</span></p>
${end}
<form method="post" action="${action}" accept-charset="UTF-8">
<input type="hidden" name="target" value="${target}" />
${if token}
Bitte geben Sie Ihr Token ein:<br/>
<input type="text" name="token" autofocus /><br/>
<br/>
<input type="submit" value="Verifizieren" /><br/>
${else}
Benutzername:<br/>
<input type="text" name="username" autofocus /><br/>
Passwort:<br/>
<input type="password" name="password" /><br/>
<br/>
<input type="submit" value="Login" /><br/>
${end}
</form>
As you might have guessed, this one file is used to create
- the login dialog,
- the token input dialog and
- pages displaying error messages.
Attributes
| Name | Mandatory | Description | Example |
|---|---|---|---|
| login | yes | context path of the login dialog | /login/ |
| location | yes | location of the login dialog template (a directory containing the index.html file as well as possibly other resources) | file:c:/work/login/ |
Child Elements
| Name | Description |
|---|---|
| staticUserDataProvider | A user data provider listing all user data in-place in the config file. |
| ldapUserDataProvider | A user data provider querying an LDAP server to authorize users and retrieve attributes. |
| unifyingUserDataProvider | A user data provider that consists of two or more other user data providers. |
| sessionManager | The sessionManager. (Default values will be used, if the element is not specified.) |
| accountBlocker | The accountBlocker. (Default values will be used, if the element is not specified.) |
| telekomSMSTokenProvider | A token provider using Deutsche Telekom's REST interface developer garden to send a randomly generated numeric token to the user via text message. |
| totpTokenProvider | A token provider using the Time-based One-time Password (TOTP) algorithm specified in RFC 6238 to verify tokens using a pre-shared secret. |
Example
The login example contained in the distribution demonstrates a simple setup usind the staticUserDataProvider and the totpTokenProvider.